Build a policy lifecycle solution with SharePoint and Microsoft 365 – Part 2
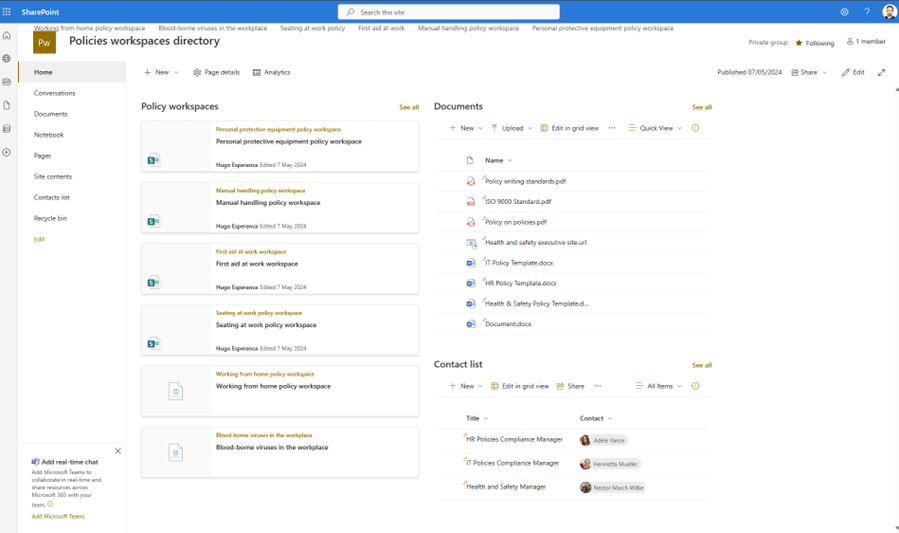
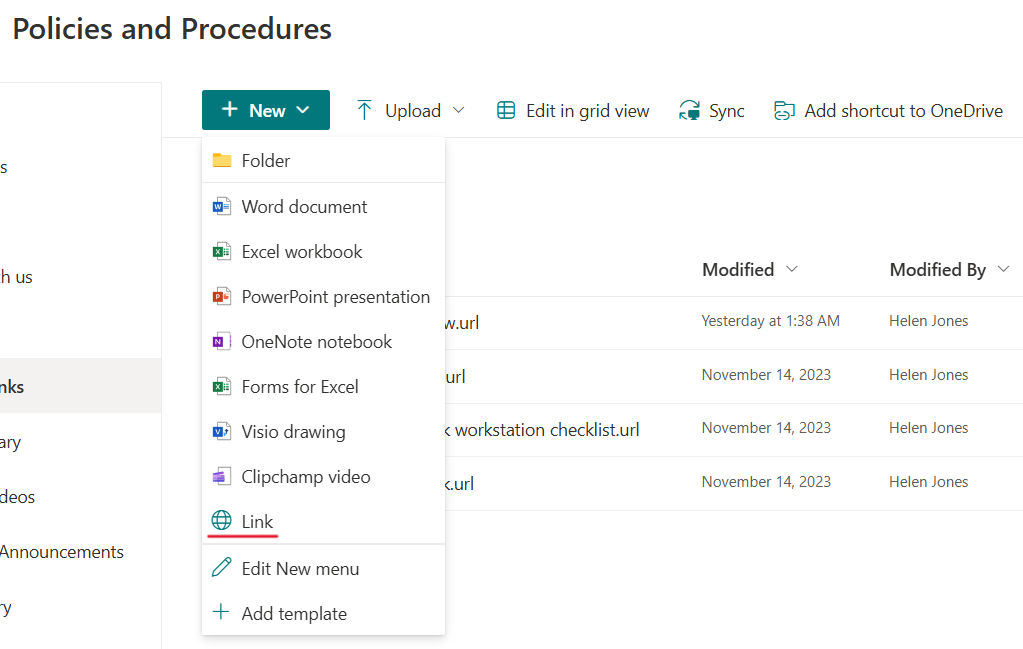
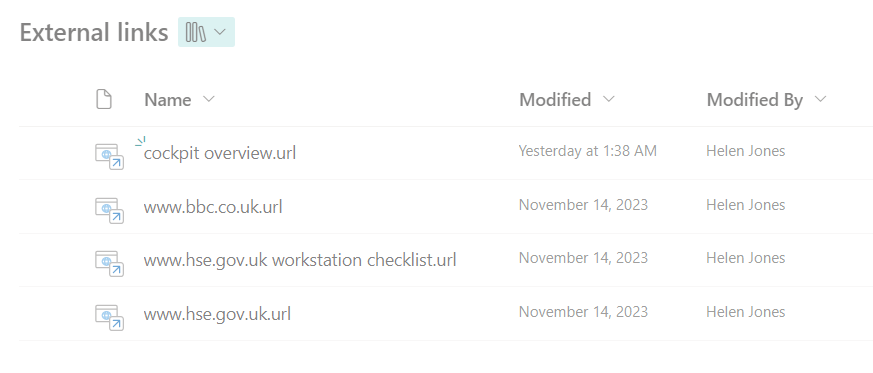
Build a policy lifecycle solution with SharePoint and Microsoft 365 – Part 2Welcome to part two of this series explaining how to create an effective policy lifecycle. Click here to read part one if you missed it. How to create a policy lifecycle solution with SharePoint and Microsoft 365 – seriesResearch and createCollaborate and approve […]
Read more