Creating a Policy Approval Workflow with Power Automate
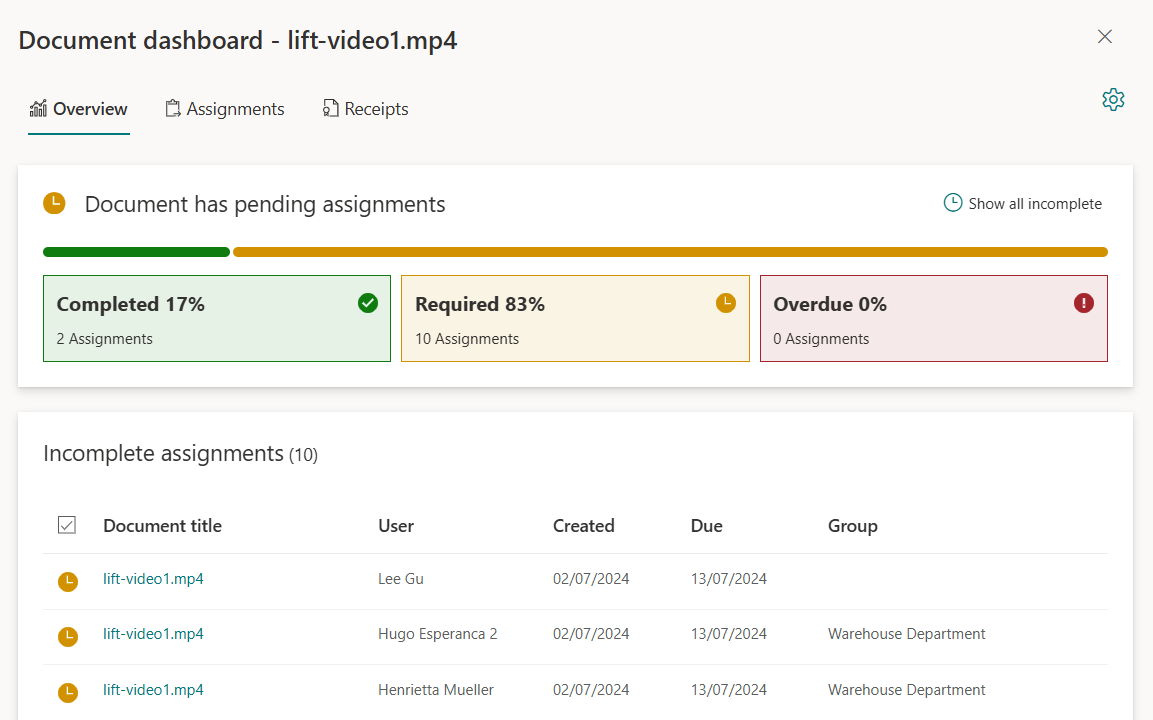
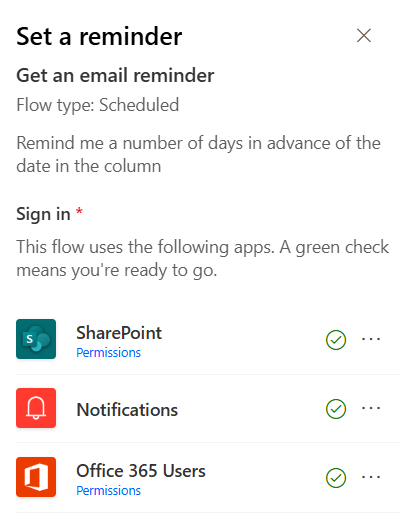
Policy Approval WorkflowAutomated policy approval workflows offer several benefits that can significantly enhance the efficiency and accuracy of policy creation within an organization. Here are some of the key advantages:Increased Efficiency: Automation speeds up the document approval process by eliminating manual steps. This results in quicker turnaround times for document approvals.Reduced Errors: Automated workflows minimize […]
Read more